What to Know About The Microsoft “Permissions Requested” Pop-Up For Apps
We receive countless emails and browser or app pop-up windows in our daily work, some legitimate and some not. It is becoming more challenging to discern the difference. The bad actors are getting better at matching the fonts and logos of real companies with whom we do business, spoofing email addresses, and generally appearing legitimate. Being on guard is essential.
This new “Permissions requested” app pop-up is pretty simple to recognize, at least for now. If you see the screen (shown here to the right on desktop screens) in your daily work, stop and review it carefully. Unless you have been specifically directed, it is most certainly not legitimate.
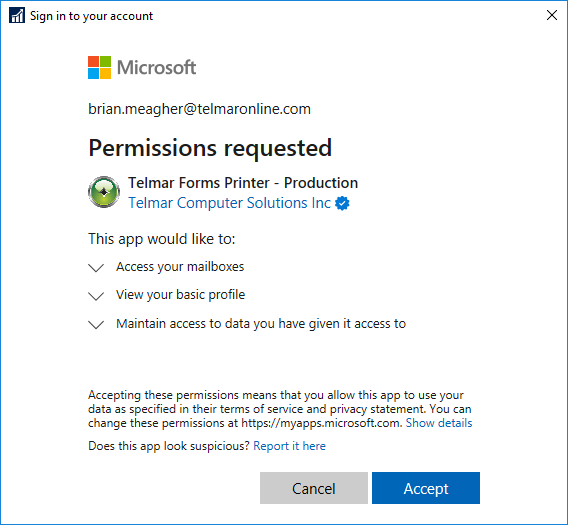
The bad actors are crafting these requests to seem necessary for basic tasks. Unfortunately, clicking “Accept” ultimately grants access to your emails, calendars, files, and other things stored in Microsoft’s cloud.
A single click could grant the bad actor full access to your data.
User Education is Key
Gartner states that 85% of data breaches involve a human element, sometimes called social engineering. That means end users are the biggest risk to a company’s data. That makes user education critical.
Countless services use Microsoft’s Enterprise Applications. The power and flexibility they enable can provide amazing solutions for modern businesses, but not without potential risk. A quick review of Telmar’s current enterprise apps includes our Office 365 backup solution, a custom application for emailing invoices, and a tie into Exchange from our leave tracking software, among others. The key is to educate users on the potential risks and what steps to take if they see a prompt like this “Permissions requested” pop-up example.
If your organization is struggling with technology challenges related to your ERP system, please Contact Us. Telmar has decades of experience dealing with these types of issues. We love to help our clients in whatever way we can.
Did You Know
NEED HELP MAKING YOUR DYNAMICS GP ENVIRONMENT SIMPLER TO MANAGE?
Other Posts You May Be Interested In…
Partner Spotlight: Impacts of a Data Breach
Recent data breaches have put both large and small companies on high alert. A data breach can not only harm a company financially, but also damage their reputation and impact clients’ trust. Nodus, a valued Telmar partner, has provided an excellent summary of the key points management needs to know about the impacts of a data breach. It is easy to pretend this won’t happen to your company, but it is best to assume it will.
How to Change Your Password in Dynamics GP
There are multiple reasons to change your password in Dynamics GP. If you suspect that someone knows your password, or if your password was just issued to you, it is a good idea to change it to something that only you know. In this article, you'll learn how to change your Dynamics GP password.
A Guide to Successful Project Management
A simple guide to successful project management including a preparation checklist, what to look for in a project manager and tips for minimizing risk.



0 Comments